About Us
Executive Editor:Publishing house "Academy of Natural History"
Editorial Board:
Asgarov S. (Azerbaijan), Alakbarov M. (Azerbaijan), Aliev Z. (Azerbaijan), Babayev N. (Uzbekistan), Chiladze G. (Georgia), Datskovsky I. (Israel), Garbuz I. (Moldova), Gleizer S. (Germany), Ershina A. (Kazakhstan), Kobzev D. (Switzerland), Kohl O. (Germany), Ktshanyan M. (Armenia), Lande D. (Ukraine), Ledvanov M. (Russia), Makats V. (Ukraine), Miletic L. (Serbia), Moskovkin V. (Ukraine), Murzagaliyeva A. (Kazakhstan), Novikov A. (Ukraine), Rahimov R. (Uzbekistan), Romanchuk A. (Ukraine), Shamshiev B. (Kyrgyzstan), Usheva M. (Bulgaria), Vasileva M. (Bulgar).
Engineering
Basis of the system is made by approach [1,2,3,4] virtualizations of process of the protected telecommunication.
Terms of virtualization:
1. Reports of source are i- mi by the selections of the stationary Gausse Markoff casual process.
2. The reports of source are exposed to digital treatment the result of that is distorted by noise of digital presentation.
3. Forming of cryptograms presents the result of additive distortion of reports some noise.
These terms and criterion of a minimum of middle square of error allow to get expression for the algorithm of estimation
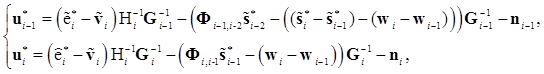
here ![]() - estimation of report;
- estimation of report; ![]() - virtual cryptogram;
- virtual cryptogram; ![]() - vectorial sequences;
- vectorial sequences; ![]() - matrices of functions.
- matrices of functions.
The distinctive feature of the schematics got from an algorithm is absence of limitations of information generator.
Functioning of transmitter part of the system is divided into three basic stages: 1) forming of virtual reports; 2) forming of the virtual keys and encipherement; 3) forming of virtual cryptograms.
Functioning of receiving part of complex is divided into the stages: 1) devirtualization cryptograms; 2) forming of the virtual keys and base decoding; 3) demultiplexing of decoding; 4) dual-link forming of reports (decoding); 5) estimation of reports.
For providing of security of process of implementation of transformations of the worked out programmatic complex and impossibility of access from the side of hardwarily-programmatic environment hardware representation of receiving and transmitter part of the system is envisaged on the base of microcontrollers.
2. Kotenko VV., Rumyantsev KE. Theory of Information and Protection of telecommunications: Monograph. - Rostov-on-Don: Southern Federal University Publishing House, 2009. -369 p.
3. Kotenko VV Theoretical Foundations of virtualization representation of objects, phenomena and processes // Information countering of terrorism threats: scientific-practical magazine. 2011, №17. P. 32-48
4. Kotenko VV. Virtual assessments theoretical justification of protected telecommunications // XI International scientific-practical conference "Information Security". Part 1 - Taganrog: Publishing house of the TTI SFU, 2010. P. 177-183.
5. Kotenko VV Virtualization continuous data protection process with respect to the theoretical conditions nedeshifruemosti / Information counter the threats of terrorism. 2013. № 20. P.140-147.
6. Kotenko VV, Kotenko SV Identification analysis of cryptographic algorithms from the point of virtualization IDs / Proceedings of the SFU. Technical science. 2015. number 8 (169). P. 32-46.
7. Kotenko VV, Kurt AR encryption algorithm model with virtualization assessments / International Journal of Experimental Education. 2015. № 8-3. P. 411-412.
8. Kotenko VV Virtualization continuous data protection process with respect to the theoretical conditions nedeshifruemosti / Information counter the threats of terrorism. 2013. № 20. P. 140-147.
9. Kotenko VV, Kotenko SV, Rumyantsev KE, Gorbenko YI continuous data protection strategy with a key position in the band virtualization formal relations ensembles. Applied electronics. 2013. T. 12. № 3. P. 308.
10. Kotenko SV, Kotenko VV Methods of identification analysis of error-correcting coding in encoding processes for continuous channel / Information counter the threats of terrorism. 2013. № 20. P.151-157.
11. Kotenko SV Pershin IM Kotenko VV Features of identification analysis on the basis of information in the GIS objects virtualization location images. Proceedings of SFU. Technical science. 2014. № 8 (157). P. 212-219.
12. Kotenko VV Information quantization / Information counter the threats of terrorism. 2007. № 9. P. 97-99.
13. Kotenko VV Information evaluation of the quality of communication / Information counter the threats of terrorism. 2007. № 9. P. 50-55.
14. Kotenko VV Coding theorem for discrete channel with continuous transfer of information sources / Information counter the threats of terrorism. 2007. № 9. P.184-187.
15. Kotenko VV The theoretical justification of virtual assessments of protected telecommunications // Proceedings of the XI International Scientific and Practical Conference "Information Security". Part 1 - Taganrog: Publishing House of TTI SFU, 2010. - P. 177-183.
16. Kotenko VV Strategy for the use of information flows virtualization theory for solving information security problems // Bulletin of SFU. Technical science. - 2007. - V. 76. - № 1. - P. 26-37.
Kotenko V.V., Polyakov A.I., Rumyantsev K.E., Evterev A.G. THE SYSTEM OF DEFENCE IS THE INTERNET OF RESOURCES OF PRODUCTION AMALGAMATION. International Journal Of Applied And Fundamental Research. – 2016. – № 2 –
URL: www.science-sd.com/464-25194 (28.02.2026).










 PDF
PDF