About Us
Executive Editor:Publishing house "Academy of Natural History"
Editorial Board:
Asgarov S. (Azerbaijan), Alakbarov M. (Azerbaijan), Aliev Z. (Azerbaijan), Babayev N. (Uzbekistan), Chiladze G. (Georgia), Datskovsky I. (Israel), Garbuz I. (Moldova), Gleizer S. (Germany), Ershina A. (Kazakhstan), Kobzev D. (Switzerland), Kohl O. (Germany), Ktshanyan M. (Armenia), Lande D. (Ukraine), Ledvanov M. (Russia), Makats V. (Ukraine), Miletic L. (Serbia), Moskovkin V. (Ukraine), Murzagaliyeva A. (Kazakhstan), Novikov A. (Ukraine), Rahimov R. (Uzbekistan), Romanchuk A. (Ukraine), Shamshiev B. (Kyrgyzstan), Usheva M. (Bulgaria), Vasileva M. (Bulgar).
Engineering
Internet GIS is a system that performs basic manipulation with spatial data on a dedicated web-map server and providing this data to users via the Internet Protocol compatible with HTTP [1].
Security Internet GIS depends largely on the security of the web server on which it is based [2].
The security level of GIS depends on the objectives of this geographic information system by the user. You can consider the use of the system at the household level, and the study of specific tasks performed by a specialist.
1. The use of geographic information systems at a basic level
If at the beginning the advent of the Internet (last century) and he himself, and, especially, geographic information systems, was inaccessible for the masses, then gradually, they became more and more popular. So, a large spread in the beginning of the XXI century received various interactive maps (Yandex.Maps, 2GIS, etc.) that are used when finding the route to a certain point, information about the object that is in a known location. Often used and additional features such as GIS: for example, you can find out which objects are close to the selected point, where there are objects with certain properties, etc.
For example, in planning a tourist trip it is possible to learn using GIS (or search engines on the Internet without GIS), what is the cost of the hotel rooms in the hotels of this locality. You can also plan your travel route, find out what attractions are within the route. In [8] an example of a geo-portal for tourism topics, created using geographic information systems.
Geoportal in General perceived as an Internet resource, which is used to find and access geographic (spatial) data. They come in different geographic coverage (national, regional and local), and on the subject of [8].
The technical characteristics of the geoportals also different. For example, some provide only cards of different routes and different places the second card, and other text and multimedia information about the area, and others – interactive map with metadata (information related to objects on the map). In tourism practice becoming more popular today are the geoportal with an interactive map and metadata.
To the end user of the geoportal as a web site that provides directly in the web interface tools for searching and exploring geographic data.
Figure 1 shows a fragment of the resource Yandex.Maps marked with the locations of the museums.
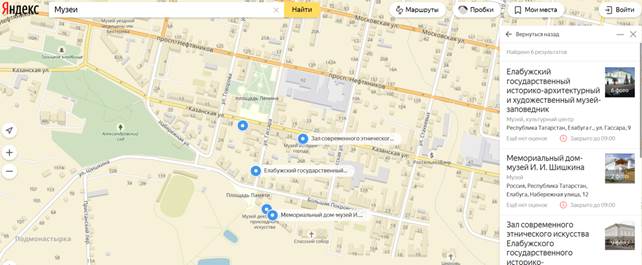
Figure 1. Museums on the resource Yandex.Maps
Convenient and other GIS functions: for example, we can know exactly where an Agency, its hours of operation and routes of travel by different modes of transport.
Figure 2 provides a window of 2GIS resource with information about the Museum and its location on the map.
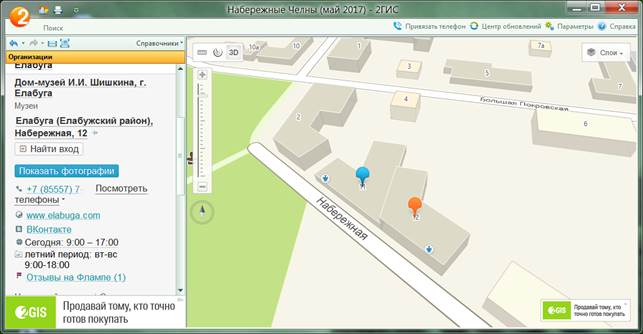
Figure 2. Information about the Museum on the resource 2GIS
Thus, the use of Internet GIS in their daily activities without the use of high-precision maps. At this level, you can use the built-in GIS tools of information protection, and in the case of using Internet GIS – basic security information the Internet.
2. The use of geographic information systems at the specialist level
If at the basic level, the issue of information protection is almost not worth it, when the work of the expert in protection of information depends on the level of privacy of the challenges facing the particular specialist.
When you select a geographic information system it is necessary to consider the specific tasks that the user intends to solve with the help of this system. If the problem is rather complicated, it is advisable to develop your own version of the GIS, using the GIS in conjunction with it.
Consider the potential threats to Internet GIS [2].
First, it is an attack via the Internet to unauthorized access, modification or retention of information.
Secondly - unauthorized use of data obtained through legal use of a GIS.
Thus, it is possible to select the following areas of protection:
1. maximum protection the Internet server from unauthorized access, changes and data hold;
2. giving users only the data, reuse of which in commercial products is eliminated [1].
Additionally, you can use cryptographic encryption to protect the map data.
Makes sense creating your own map server. It is possible to allocate two directions of implementation of the online map server:
• using standard GIS;
• self realization of the elements of the GIS Internet server.
Depending on the technology strategies and platforms web GIS servers can be divided into several groups [1], [2]:
1. The servers that transmit the source data to the client computer (FTP, HTTP-servers). Further files are processed by the GIS application available on the client computer.
2. The servers that transmit the geographical static image in raster or vector format.
3. Servers that handle requests to the metadata using a mapping of the image.
4. The server that generates maps online. This is the most popular method of transfer of the geoimage data. The use of such technology allows to interactive maps, meeting any needs of the user in the framework provided him opportunities.
When using Internet-GIS should be borne in mind that the user requests can be stored in the system or transferred to third parties, so that when processing restricted information should not use public GIS, and ideally – do not use the Internet at all, and use only the internal network.
You can suggest the following ways to protect information [7].
First, it must be authorized entrance in the geographic information system has great potential in the Internet.
Second, information in a GIS must be transmitted over protected channels.
Thirdly, the secret items should not appear on the maps provided to persons having the right of access to classified information.
Finally, the restricted information may be stored and transmitted in encrypted form.
Using these precautions, we can reduce the probability of intercept GIS information, and to prevent the harm from its dissemination.
Thus, we considered the possibility of using Internet-GIS standard users and the specialist in any field. If the user can use the GIS without limits, the officer must use means of protection of information in their research. In some cases, the built-in GIS tools, in other cases it is necessary to apply additional means such as data encryption. It depends on the degree of confidentiality of processed specialist information.
2. Mironova Yu.N. Geoinformacionnye sistemy i internet // Molodoj uchenyj. №9.1 (89.1), maj-1 2015 g., s. 40-42. URL: http://moluch.ru/archive/92/17769/
3. Mironova Yu.N. Geographic information systems and their classification // International Journal Of Applied And Fundamental Research. – 2016. – № 1 – URL: www.science-sd.com/463-24961 (26.04.2016).
4. Mironova Yu.N. Virtual modeling in geoinformation technologies // International Journal Of Applied And Fundamental Research. – 2016. – № 2 – URL: www.science-sd.com/464-24988 (09.08.2016).
5. Mironova Yu.N. The classification of geoinformation objects // International Journal Of Applied And Fundamental Research. – 2016. – № 2 – URL: www.science-sd.com/464-25151 (29.09.2016).
6. Mironova Yu.N. The study of geoinformatics with the use of gaming moments // International Journal Of Applied And Fundamental Research. – 2016. – № 3 – URL: www.science-sd.com/465-25000 (09.08.2016).
7. Mironova Yu.N. Geographic information systems and confidentiality of information // European Journal Of Natural History. - 2016. - № 5. С. 48-49. URL: www.world-science.ru/euro/519-33634 (01.09.2016).
8. Safarjan A.A. Turistskij geoportal kak instrument vizualizacii rezul'tatov issledovanija i prodvizhenija destinacii // Servis v Rossii i za rubezhom. 2016. T. 10. № 4 (65). S. 56-70.
9. Internet resurs «Geoinformatika. Pod redakciej prof. B.C. Tikunova. M.: «Akademija», 2005» http://www.studfiles.ru/preview/1817795/
Mironova Y.N. THE USE OF INTERNET GIS AND THE PROBLEMS OF INFORMATION SECURITY. International Journal Of Applied And Fundamental Research. – 2018. – № 1 –
URL: www.science-sd.com/473-25383 (28.02.2026).










 PDF
PDF